In the realm of network communication, two fundamental processes ensure the seamless transfer of data between devices: encapsulation and decapsulation. These processes are the backbone of how information is packaged, transmitted, and received across networks, playing a pivotal role in maintaining the integrity and security of data as it journeys through the complex web of internet protocols and devices.
Encapsulation is the process by which data is wrapped with necessary protocol information before transmission, ensuring it can travel from source to destination across diverse network environments. Decapsulation, on the other hand, is the method of removing this added information upon arrival at the destination to retrieve the original data. Together, they enable the accurate and efficient exchange of information across the internet.
This discussion focuses on the intricacies of how encapsulation and decapsulation function within network communication. By understanding these processes, one gains insight into the foundational elements that keep our digital world interconnected, ensuring that data not only reaches its intended destination but does so securely and efficiently.
Basics of Networking
Networking forms the backbone of how computers, servers, and other digital devices communicate with each other over distances. It’s the structured practice of linking devices using physical and wireless technologies, following set protocols to manage and maintain data exchange.
Encapsulation Overview
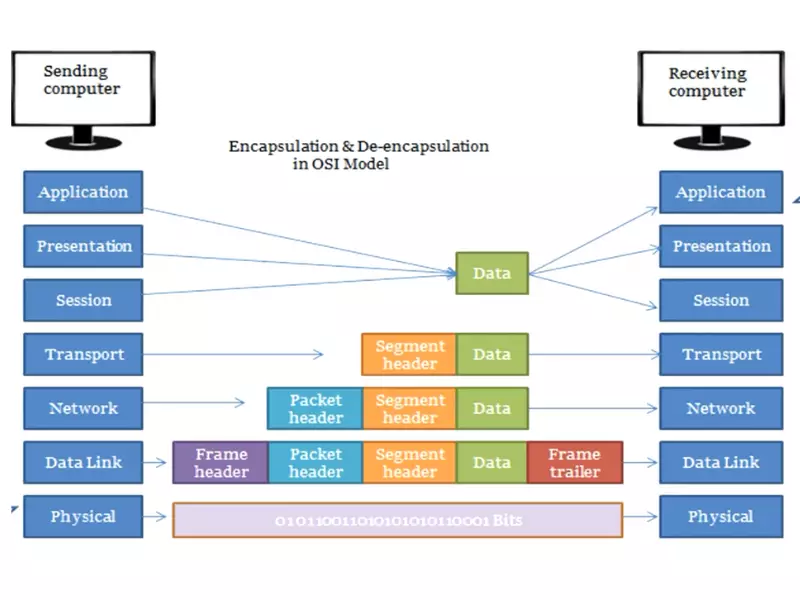
Encapsulation is a core process in networking, crucial for data transmission. It involves wrapping data with necessary protocol information before it’s sent over a network. This protocol information, often in the form of headers and trailers, tells the network how to handle the data packet, including where to send it and how it should be treated upon arrival.
How It Works
- Data from an application is passed down through the network layers.
- Each layer adds its own header (or trailer) with specific protocol information.
- The result is a data packet ready for transmission across the network.
Roles and Benefits
Security and Efficiency
Encapsulation enhances security by keeping data packets intact and unreadable to unauthorized users. It also increases efficiency in data transmission, as each layer’s protocol information directs the packet precisely where it needs to go.
Data Integrity
Data integrity is maintained through encapsulation, ensuring the data that reaches the destination is exactly what was sent, without alteration or corruption.
Decapsulation Overview
Decapsulation is the reverse process of encapsulation. It involves stripping away the added protocol information layer by layer as the data packet moves up through the network layers at the destination.
Process Explained
- The data packet arrives at the destination’s network layer.
- Each layer removes its corresponding header or trailer, extracting the original data.
- The data is finally delivered to the appropriate application in its original form.
Roles and Benefits
Accurate Data Interpretation
Decapsulation ensures that the receiving device accurately interprets the data as intended by removing the encapsulation layers.
Seamless Communication
It enables seamless communication between devices, as data is accurately reconstructed and delivered to the correct application.
Core Principles
Data Transmission Process
The data transmission process in networking is a systematic approach to sending and receiving data between devices. It’s grounded in the principles of encapsulation and decapsulation, ensuring data is packaged securely and arrives intact.
Importance in Networking
Encapsulation and decapsulation are not just technical processes; they’re foundational to the operation and reliability of modern networks. They ensure that data can travel across diverse network environments—be it wired or wireless, local or global—safely and efficiently.
Encapsulation Detailed
Understanding encapsulation in detail reveals its critical role in networking. It’s a layered approach, with each layer of the network adding its own set of instructions to the data packet. This structuring is what makes data transmission across networks both possible and practical.
How It Works
- Application Layer Data: Starts with user data that needs to be transmitted.
- Layer-by-Layer Wrapping: Each network layer adds its header, with specific protocol rules.
- Packet Formation: The fully wrapped data packet is then ready for transmission.
The beauty of encapsulation lies in its simplicity and effectiveness. By systematically adding protocol information, it ensures that every piece of data is correctly routed, handled, and delivered across complex network architectures.
Roles and Benefits
The process of encapsulation plays several key roles and brings numerous benefits to network communication:
- Protocol Management: Ensures data adheres to specific network protocols, facilitating interoperability and standardization.
- Security: Protects data during transit, preventing unauthorized access and data breaches.
- Efficiency: Optimizes network performance by enabling the precise routing of packets.
- Data Integrity: Guarantees that the data received is exactly as sent, without errors or modifications.
Decapsulation Detailed
Decapsulation complements encapsulation, ensuring that the communication cycle is completed successfully by accurately reconstructing the transmitted data upon arrival.
Process Explained
The process of decapsulation mirrors encapsulation but in reverse order:
- Receipt of Data Packet: The encapsulated packet is received by the destination device.
- Layer-by-Layer Removal: Each network layer removes its corresponding header or trailer, revealing the layer beneath.
- Data Delivery: The original data is extracted and delivered to the appropriate application.
This meticulous stripping of headers and trailers at each layer ensures that the data is interpreted correctly and functions as expected on the receiving end.
Roles and Benefits
Decapsulation ensures that data transmitted across a network is usable upon arrival, which is vital for:
- Accuracy: Ensures that the data is precisely as it was before encapsulation.
- Functionality: Allows applications to receive and process data without needing to understand the complexities of network protocols.
- Seamless Communication: Facilitates the smooth exchange of information between devices, crucial for network services and applications to function correctly.
Comparison
Key Differences
Encapsulation and decapsulation serve as the bookends of data transmission in networking, each with distinct roles yet inherently connected. The key differences lie in their process orientation and functional objectives.
Process Orientation
- Encapsulation involves adding protocol information to data as it descends through the network layers, preparing it for transmission.
- Decapsulation removes this protocol information layer by layer as data ascends to its destination application, making it readable and usable.
Functional Objectives
- Encapsulation aims to secure and efficiently route data across networks.
- Decapsulation’s goal is to retrieve and interpret the original data correctly.
Table Summary
| Feature | Encapsulation | Decapsulation |
|---|---|---|
| Process | Adds protocol information | Removes protocol information |
| Direction | Data descends through layers | Data ascends through layers |
| Objective | Secure routing and efficiency | Accurate data interpretation |
| Outcome | Data packet ready for transmission | Original data ready for application |
Use Cases
Encapsulation in Action
VPNs and Secure Transmissions
VPNs (Virtual Private Networks) exemplify encapsulation. They secure data by wrapping it in an encrypted layer, making it unreadable to outsiders as it travels across the internet. This process is pivotal for maintaining privacy and security in data transmission, especially over unsecured networks.
Decapsulation in Practice
Receiving Data on Devices
Decapsulation is critical when devices receive data. It ensures that the data, once it arrives, is stripped of its transmission protocols and is in a format that the receiving application can use and understand. This process is fundamental for everyday tasks, such as browsing the web or checking email.
Advanced Concepts
Protocols Involved
TCP/IP Model Layers
The TCP/IP model, foundational to internet communications, relies heavily on encapsulation and decapsulation. Each of its layers, from the Application down to the Network Interface, plays a role in preparing data for the journey through a network or interpreting it upon arrival.
OSI Model Relevance
The OSI (Open Systems Interconnection) model, with its seven layers, provides a more detailed view of where and how encapsulation and decapsulation occur. Understanding these models is key to grasping the complexity and nuance of network communications.
Real-World Applications
Networking Devices and Software
Devices like routers, switches, and firewalls use encapsulation and decapsulation to manage data flow. Networking software, including operating systems and communication protocols, also relies on these processes to ensure data is handled correctly.
Challenges and Solutions
Common Issues in Encapsulation
- Overhead: Each layer of encapsulation adds bytes to the data packet, potentially leading to bandwidth inefficiency.
- Complexity: Managing different protocols and standards can be challenging, requiring sophisticated software and hardware solutions.
Addressing Decapsulation Problems
- Data Corruption: Errors during transmission can complicate decapsulation, requiring mechanisms like error checking and correction.
- Protocol Misinterpretation: Ensuring that decapsulation correctly interprets each layer’s protocol information demands rigorous standardization and compatibility.
Future Outlook
Trends and Innovations
The future of encapsulation and decapsulation lies in innovation and adaptation. With the rise of technologies like 5G, IoT (Internet of Things), and cloud computing, these processes must evolve to handle increased volume, speed, and complexity of data transmission.
Impact on Network Security
As digital threats become more sophisticated, the role of encapsulation in network security becomes more crucial. Future developments are likely to focus on enhancing encryption and anonymity in data transmission, ensuring that encapsulation not only serves its traditional roles but also becomes a formidable barrier against cyber threats.
Frequently Asked Questions
What is Encapsulation in Networking?
Encapsulation in networking is a method used to wrap data with necessary protocol information before it is transmitted over a network. This process allows data to navigate through the network by providing it with the necessary routing and delivery instructions, ensuring it reaches its intended destination correctly and securely.
How Does Decapsulation Work?
Decapsulation works by removing the protocol information added during the encapsulation process, which occurs once the data reaches its destination. This step is crucial for the receiving device to interpret and utilize the original data, stripping away the added headers and trailers to access the core information needed.
Why Are Encapsulation and Decapsulation Important?
Encapsulation and decapsulation are vital for the functionality of network communications, ensuring data integrity, security, and efficient delivery across different network layers. These processes allow for the structured and systematic handling of data, facilitating compatibility and communication between different network protocols and architectures.
Can Encapsulation Affect Network Performance?
Yes, encapsulation can affect network performance. While it is essential for data security and routing, adding extra headers or trailers increases the packet size, which can consume more bandwidth and increase processing time. However, efficient encapsulation protocols are designed to minimize these impacts and ensure smooth network operations.
Conclusion
The intricate dance between encapsulation and decapsulation forms the core of network communication, enabling the digital conversations that power our modern world. These processes not only ensure that data is securely and efficiently transmitted across various networks but also maintain the integrity of the information as it traverses the complex internet infrastructure.
As we delve deeper into the age of digital communication, the roles of encapsulation and decapsulation become increasingly crucial, underscoring the importance of understanding these fundamental concepts in the realm of network engineering and cybersecurity. Through their continuous evolution, we can look forward to more robust, secure, and efficient network communication systems that will shape the future of digital interactions.
